Researchers Aim to Prevent Medical Imaging Cyberattacks
Released: November 27, 2018
At A Glance
- New research addresses the potential risk of cyberattacks in medical imaging.
- Researchers from Israel developed a system to send an alert if a CT machine receives a malicious command.
- Researchers from Switzerland trained an artificial intelligence network to alter mammograms.
- RSNA Media Relations
1-630-590-7762
media@rsna.org - RSNA 2018 Newsroom
(Nov. 24-29, 2018)
1-312-791-6610 - Maureen Morley
1-630-590-7754
mmorley@rsna.org - Linda Brooks
1-630-590-7738
lbrooks@rsna.org
CHICAGO — Two new studies being presented this week at the annual meeting of the Radiological Society of North America (RSNA) address the potential risk of cyberattacks in medical imaging.
The Internet has been highly beneficial to health care—radiology included—improving access in remote areas, allowing for faster and better diagnoses, and vastly improving the management and transfer of medical records and images. However, increased connectivity can lead to increased vulnerability to outside interference.
Researchers and cybersecurity experts have begun to examine ways to mitigate the risk of cyberattacks in medical imaging before they become a real danger.
Medical imaging devices, such as X-ray, mammography, MRI and CT machines, play a crucial role in diagnosis and treatment. As these devices are typically connected to hospital networks, they can be potentially susceptible to sophisticated cyberattacks, including ransomware attacks that can disable the machines. Due to their critical role in the emergency room, CT devices may face the greatest risk of cyberattack.
In a study presented today, researchers from Ben-Gurion University of the Negev in Beer-Sheva, Israel, identified areas of vulnerability and ways to increase security in CT equipment. They demonstrated how a hacker might bypass security mechanisms of a CT machine in order to manipulate its behavior. Because CT uses ionizing radiation, changes to dose could negatively affect image quality, or—in extreme cases—pose harm to the patient.
"In the current phase of our research, we focus on developing solutions to prevent such attacks in order to protect medical devices," said Tom Mahler, Ph.D. candidate and teaching assistant at Ben-Gurion University of the Negev. "Our solution monitors the outgoing commands from the device before they are executed, and will alert—and possibly halt—if it detects anomalies."
For anomaly detection, the researchers developed a system using various advanced machine learning and deep learning methods, with training data consisting of actual commands recorded from real devices. The model learns to recognize normal commands and to predict if a new, unseen command is legitimate or not. If an attacker sends a malicious command to the device, the system will detect it and alert the operator before the command is executed.
"In cybersecurity, it is best to take the 'onion' model of protection and build the protection in layers," Mahler said. "Previous efforts in this area have focused on securing the hospital network. Our solution is device-oriented, and our goal is to be the last line of defense for medical imaging devices."
He added that it is also important to note that although these types of attacks are theoretically possible, there is no indication that they ever actually occurred.
"If health care manufacturers and hospitals will take a proactive approach, we could prevent such attacks from happening in the first place," he said.
A second study, to be presented tomorrow, looked at the potential to tamper with mammogram results.
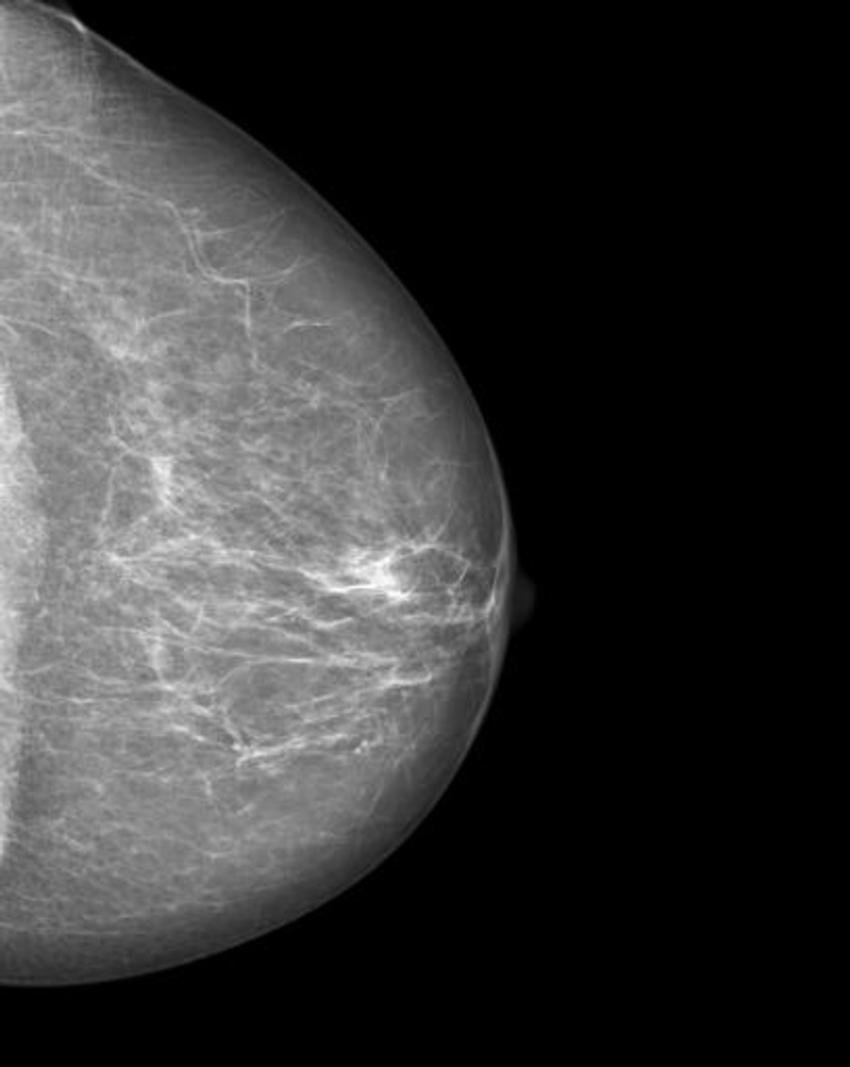
The researchers trained a cycle-consistent generative adversarial network (CycleGAN), a type of artificial intelligence application, on 680 mammographic images from 334 patients, to convert images showing cancer to healthy ones and to do the same, in reverse, for the normal control images. They wanted to determine if a CycleGAN could insert or remove cancer-specific features into mammograms in a realistic fashion.
"As doctors, it is our moral duty to first protect our patients from harm," said Anton S. Becker, M.D., radiology resident at University Hospital Zurich and ETH Zurich, in Switzerland. "For example, as radiologists we are used to protecting patients from unnecessary radiation. When neural networks or other algorithms inevitably find their way into our clinical routine, we will need to learn how to protect our patients from any unwanted side effects of those as well."
The images were presented to three radiologists, who reviewed the images and indicated whether they thought the images were genuine or modified. None of the radiologists could reliably distinguish between the two.
"Neural networks, such as CycleGAN, are not only able to learn what breast cancer looks like," Dr. Becker said, "we have now shown that they can insert these learned characteristics into mammograms of healthy patients or remove cancerous lesions from the image and replace them with normal looking tissue."
Dr. Becker anticipates that this type of attack won't be feasible for at least five years and said patients shouldn't be concerned right now. Still, he hopes to draw the attention of the medical community, and hardware and software vendors, so that they may make the necessary adjustments to address this issue while it is still theoretical.
Dr. Becker said that artificial intelligence, in general, will greatly enrich radiology, offering faster diagnoses and other advantages. He added that there are positive aspects to these findings as well.
"Neural networks can teach us more about the image characteristics of certain cancers, making us better doctors."
Mahler's co-authors are Erez Shalom, Ph.D., Arnon Makori, M.D., Israel Goldenberg, B.Sc., Ilan Shelef, M.D., Yuval Elovici, Ph.D., and principal investigator Yuval Shahar, M.D., Ph.D. Dr. Becker's co-authors are Lukas Jendele, Ondrej Skopek, Soleen Ghafoor, M.D., Nicole Berger, M.D., Magda Marcon, M.D., and Ender Konukoglu, Ph.D.
Note: Copies of RSNA 2018 news releases and electronic images will be available online at RSNA.org/press18 beginning Monday, Nov. 26.
RSNA is an association of over 54,000 radiologists, radiation oncologists, medical physicists and related scientists, promoting excellence in patient care and health care delivery through education, research and technologic innovation. The Society is based in Oak Brook, Ill. (RSNA.org)
Editor's note: The data in these releases may differ from those in the published abstract and those actually presented at the meeting, as researchers continue to update their data right up until the meeting. To ensure you are using the most up-to-date information, please call the RSNA Newsroom at 1-312-791-6610.
For patient-friendly information on CT and mammography, visit RadiologyInfo.org.
Video (MP4):

Video 2. Footage showing a radiologic technologist preparing a patient for a CT scan and reviewing images in the control room.
Download MP4
(Right-click and Save As)

Video 4. Anton S. Becker, M.D., discusses his study on inserting or removing cancer into mammograms.
Download MP4
(Right-click and Save As)

Video 5. Anton S. Becker, M.D., discusses why he chose to conduct this research.
Download MP4
(Right-click and Save As)

Video 6. Anton S. Becker, M.D., discusses the results of his research.
Download MP4
(Right-click and Save As)

Video 7. Anton S. Becker, M.D., discusses the most surprising finding of his research.
Download MP4
(Right-click and Save As)

Video 8. Anton S. Becker, M.D., discusses what CycleGAN is and how it works.
Download MP4
(Right-click and Save As)

Video 9. Anton S. Becker, M.D., discusses what safeguards are currently in place to protect against adversarial attacks.
Download MP4
(Right-click and Save As)

Video 10. Anton S. Becker, M.D., discusses if these types of adversarial attacks have already happened.
Download MP4
(Right-click and Save As)

Video 11. Anton S. Becker, M.D., shares his advice to patients who are about to undergo mammography or another imaging exam and are worried about potential tampering.
Download MP4
(Right-click and Save As)

Video 12. Tom Mahler, Ph.D. candidate, discusses his research on medical imaging hacking.
Download MP4
(Right-click and Save As)

Video 13. Tom Mahler, Ph.D. candidate, discusses the most interesting and surprising findings of his study.
Download MP4
(Right-click and Save As)

Video 14. Tom Mahler, Ph.D. candidate, discusses why he chose to conduct this research.
Download MP4
(Right-click and Save As)

Video 15. Tom Mahler, Ph.D. candidate, gives an example of a potential attack and impact of an attack on a patient.
Download MP4
(Right-click and Save As)

Video 16. Tom Mahler, Ph.D. candidate, discusses what makes healthcare and medical imaging vulnerable to cyberattacks.
Download MP4
(Right-click and Save As)

Video 17. Tom Mahler, Ph.D. candidate, discusses what safeguards are currently in place to protect against adversarial attacks.
Download MP4
(Right-click and Save As)

Video 18. Tom Mahler, Ph.D. candidate, discusses if there has already been this kind of attack.
Download MP4
(Right-click and Save As)

Video 19. Tom Mahler, Ph.D. candidate, gives his advice to patients who are about to undergo a medical imaging exam.
Download MP4
(Right-click and Save As)
Images (JPG, TIF):
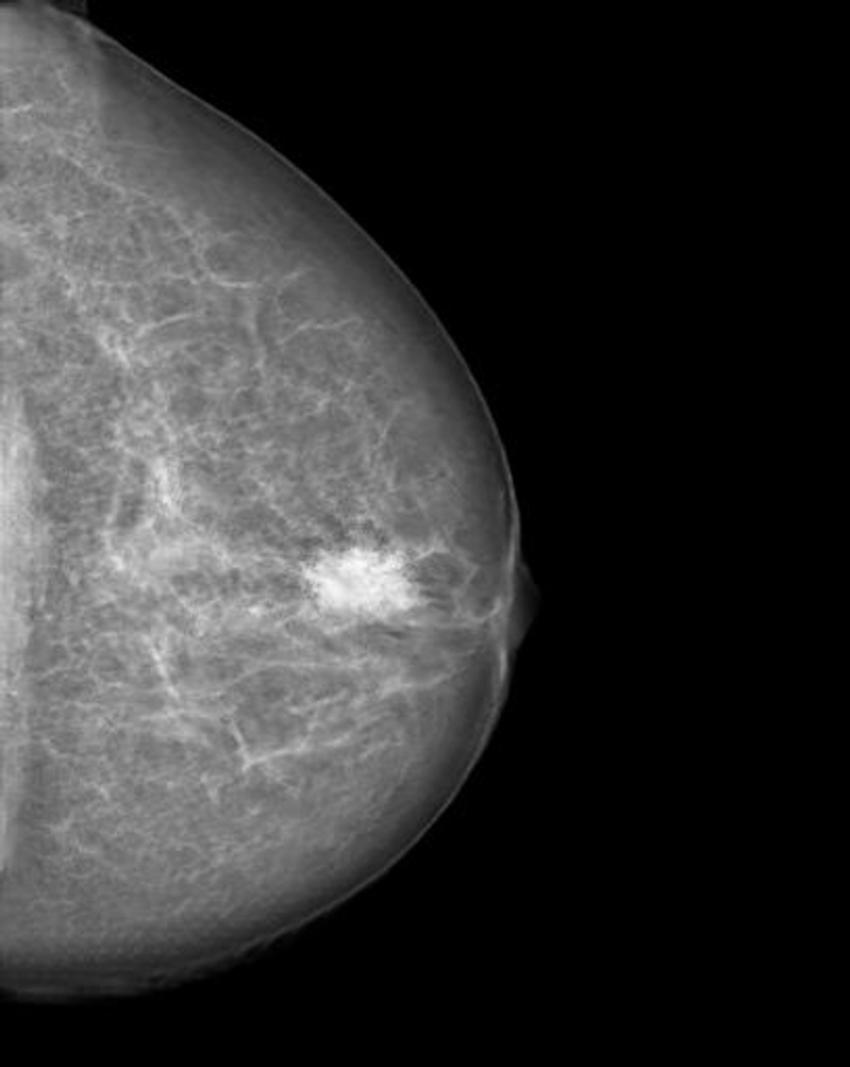
Figure 2. Manipulated mammogram of breast in Figure 1 with a neural-network-generated mass.
High-res (TIF) version
(Right-click and Save As)

Figure 4. Manipulated mammogram of breast in Figure 3 with a neural-network-generated mass.
High-res (TIF) version
(Right-click and Save As)

Figure 7. Patient undergoing CT, while technologist monitors the exam.
High-res (TIF) version
(Right-click and Save As)

Figure 8. Patient undergoing head CT, while technologists monitor the exam.
High-res (TIF) version
(Right-click and Save As)
Information for Consumers:
PowerPoint: